
- Home
- What We Do
-
-
-
OUR EXPERT AREAS
-
OTHER THINGS WE DO
-
-
- Resources
- About Us
- Careers
Well-Architected
Adopt AWS best practices and ensure your workloads are optimized for success QloudX is a certified AWS Well-Architected Partner


Is your cloud spend optimized and does it meet your budget?

Are your cloud environments protected from security threats?
The AWS Well-Architected Framework describes the design principles and architectural best practices for designing and running your workloads in the cloud. It enables you to build a secure, high-performing, flexible, and efficient infrastructure for your cloud environment and applications.
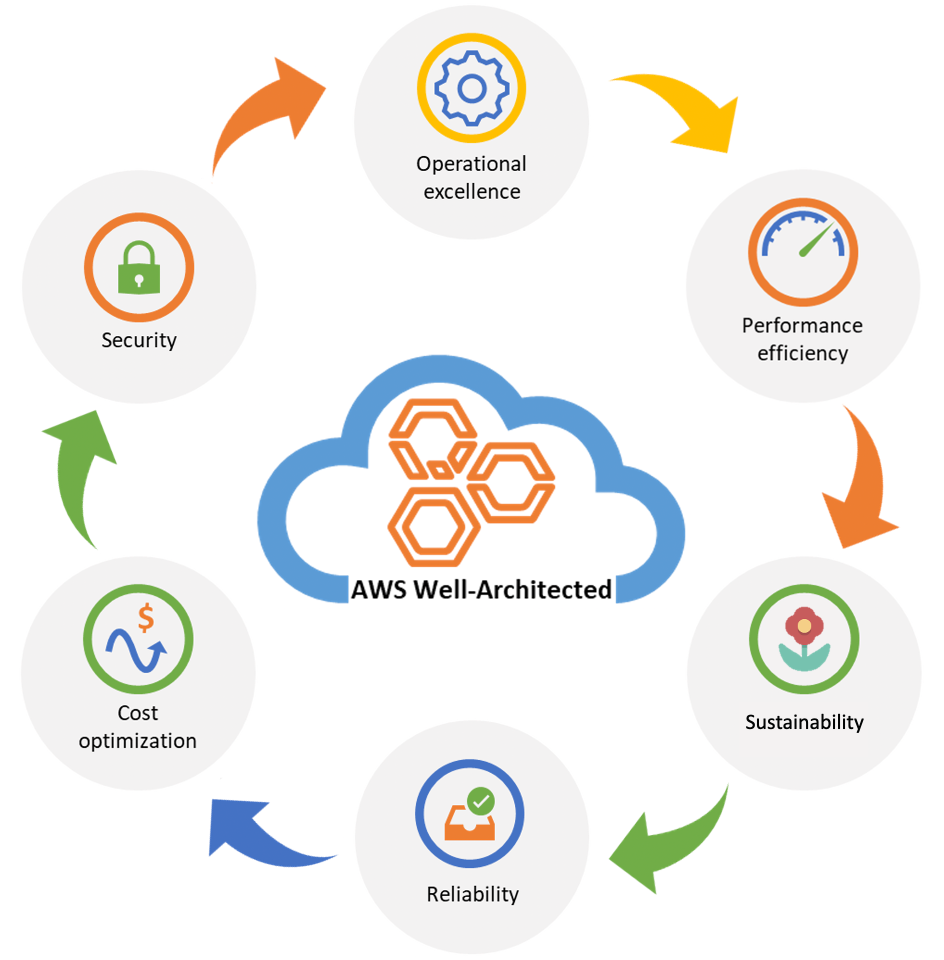
The Well-Architected Framework provides a consistent approach to evaluate architectures, and implement designs that scale with application needs over time based on six distinct pillars, each designed to help you tackle a specific aspect of your cloud environment.
Leverage QloudX's Cloud Expertise & Maximize Business Value
QloudX’s certified Cloud Engineers and Architects have deep expertise in building secure, high-performing, resilient, and efficient IT environments and creating cloud-native applications and platforms to meet your business objectives.
We are dedicated to helping businesses leverage the full potential of AWS cloud services, maintaining a strong foundation in the Well-Architected Framework in all our solutions.
AWS Well-Architected Pillars

Operational Excellence
Running and monitoring systems effectively and efficiently to deliver business value and continually improve processes and procedures

Reliability
Automating and dynamically acquiring computing resources to meet demand and recover from infrastructure or service disruptions.

Cost Optimization
Eliminating unneeded cost by right-sizing, auto-scaling, FinOps monitoring and alerting.

Performance Efficiency
Tuning cloud infrastructure using computing resources efficiently to meet system requirements as demand and technology evolve.
Sustainability
Addressing the long-term environmental, economic, and societal impact of your business activities.

Security
Protecting assets, systems, and information to deliver business value through risk assessment and mitigation strategies.
Claim your FREE AWS Well-Architected Review!
We audit your cloud environment against a set of defined Best Practices to help assess a business-critical workload against the six pillars of the Well-Architected Framework. We help you identify high-risk issues (HRIs) at no cost to you. If you after the review, wish to proceed with implementation of our recommendations and HRI (High Risk Issue) resolution, we can offer both competitive pricing and access to AWS funding to offset your costs.
An overview of the review process is given below:


Introductions
We schedule the time & place of the review, invite the required IT & business stakeholders, and identify the workload to review.
Review using the AWS Well-Architected Tool
We perform the review using the AWS Well-Architected Tool and pose questions based on the six pillars (minimum of two pillars).
Report Generation and Recommendations
We provide an in-depth report based on our findings, outlining issues and giving actionable recommendations.
Advisory and HRI Remediation*
Get support from our certified cloud experts for your chosen activities and remediation of HRIs.
*Price varies depending on size and complexity
Contact one of our Cloud Experts and Schedule your AWS Well-Architected Review
Key Benefits of the QloudX Well-Architected Review
Cost Optimization
Discover opportunities to reduce costs and eliminate wasteful spending in your AWS environment. We identify areas of inefficiency, offer cost-saving recommendations, and help you take advantage of AWS pricing models and services.
Enhanced Security
Security is paramount in the cloud. We assess your security posture, identify vulnerabilities, and recommend robust measures to protect your data and applications. Our security experts ensure compliance with industry standards and best practices.
Sustainability
As part of the Well-Architected Review, we assess your infrastructure’s sustainability and environmental impact. We provide recommendations to optimize energy efficiency, minimize carbon footprint, and adopt green initiatives. By making your AWS environment more sustainable, you can contribute to a greener future while aligning with your organization’s environmental goals.
Reliability, Performance Efficiency, and Operational Excellence
Elevate your AWS infrastructure’s reliability, application performance, and operational efficiency. We evaluate your infrastructure’s fault tolerance, disaster preparedness, and backup and recovery strategies to minimize downtime and ensure business continuity. Additionally, we analyze workload performance, optimize resource utilization, and provide recommendations for enhanced scalability, elasticity, and responsiveness.
Our AWS Badges
QloudX is recognized through a spectrum of earned competency and service delivery badges, underscoring our profound partnership with AWS and unmatched expertise.
















Our AWS Well-Architected Services
Beyond Well-Architected Reviews, we also offer a range AWS Well-Architected services. We adhere to AWS best-practices and principles in all our solutions.
With QloudX you will experience working with a partner that combines competitive pricing, unique strategic experience, expertise in cloud-native architecture, and a deep understanding of your business challenges.
Architect your cloud workloads to the best practices
Optimize your monthly cloud spend and manage budgets
Protect your cloud environment from security threats
Well-Architected Reviews
Well-Architected Reviews to obtain actionable insight into your cloud infrastructure security, reliability, and performance, as well as your cloud operations and cloud spend.
Build Well-Architected Applications
Build, migrate, and optimize architectures for secure, high-performing, reliable, and efficient applications.
Case Studies
QloudX has helped its customers reduce over 15% to 25% of their costs without compromising the performance efficiency and achieve higher reliability without any other impact on operation and security by following the Well-Architected best practices.
Read more about our Well-Architected solutions below
HOW TO GET STARTED

Ritesh Patel
Migration & Modernization Practice Lead
To start your journey with Well-Architected Cloud Solutions, contact Ritesh at godigital@qloudx.com or +91 99 248 28 699.
Ritesh has more than 17 years of experience in the IT industry spanning logistic Product development, Solution Architecture, and Data Architecture. Experience in the development of many logistic products, which includes Ocean Freight, Air Freight, Trucking, etc. For more details, check his full bio.













