Allow Restricted Public Access to Your Redshift Cluster Without Making it Public

Amazon Redshift is a fully managed, petabyte-scale data warehouse service in the AWS Cloud. An Amazon Redshift data warehouse is a collection of computing resources called nodes, which are organized into a group called a cluster. Each cluster runs an Amazon Redshift engine and contains one or more databases.
The Problem
We here at QloudX, use Redshift extensively for many of our clients. We recently came across an interesting requirement. You see, our Redshift clusters are private, for obvious security reasons. So anyone connected to our VPN can easily connect to & use the cluster. However, nobody on the public internet can access it. That’s awesome! That’s how we like it! 😊
The ask in this case however, was to connect to Redshift from a third-party application running on someone else’s servers. The diagram below shows what we need to accomplish:
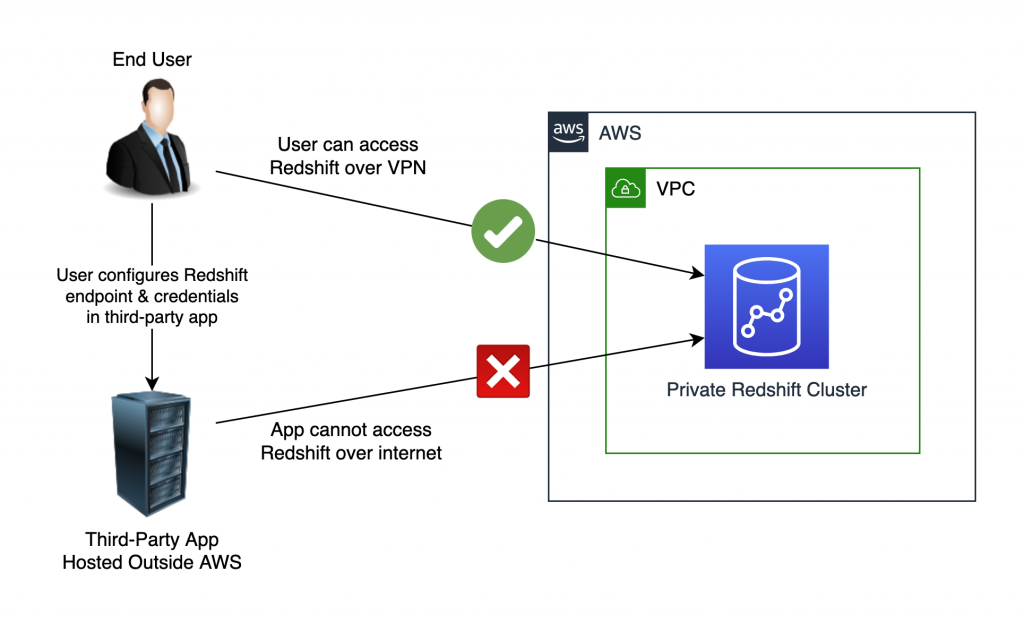
The Solution
Since making Redshift public was not an option, we decided to expose the Redshift endpoint using a Network Load Balancer instead:
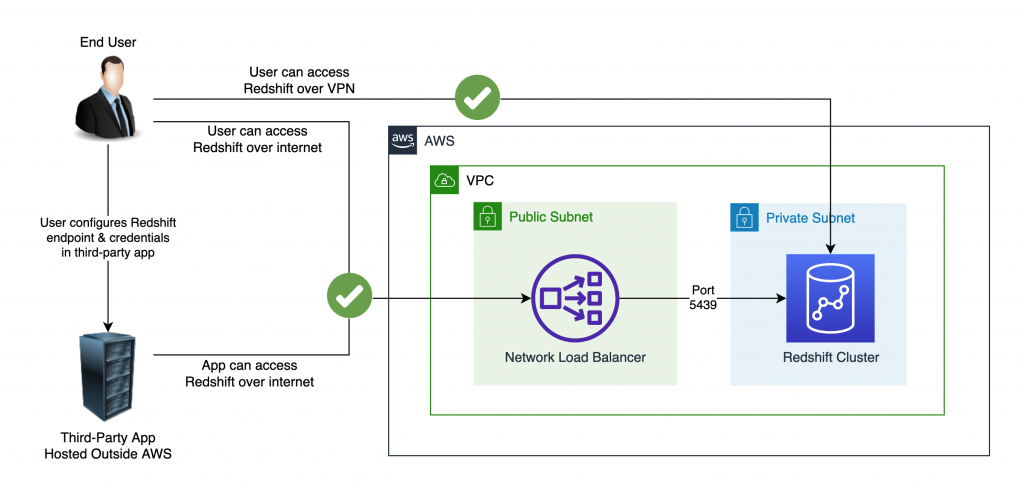
The Implementation
First, we need the private IP address of the Redshift cluster’s leader node. To get this, go to the Redshift cluster in the AWS console, switch to the Properties tab, and scroll down to find the IP addresses:
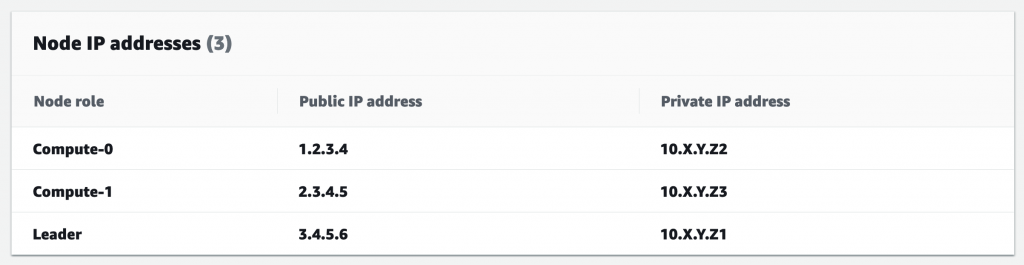
Note down the leader’s private IP 10.X.Y.Z1. You’ll need it in the next step.
This IP never changes as long as the cluster exists. Even if the leader node dies, AWS replaces it with another leader node with the same private IP!
The Target Group
Next, we create a target group pointing to this IP.
Start by visiting https://console.aws.amazon.com/ec2/v2/home#CreateTargetGroup: & select the Target Type as IP Addresses:
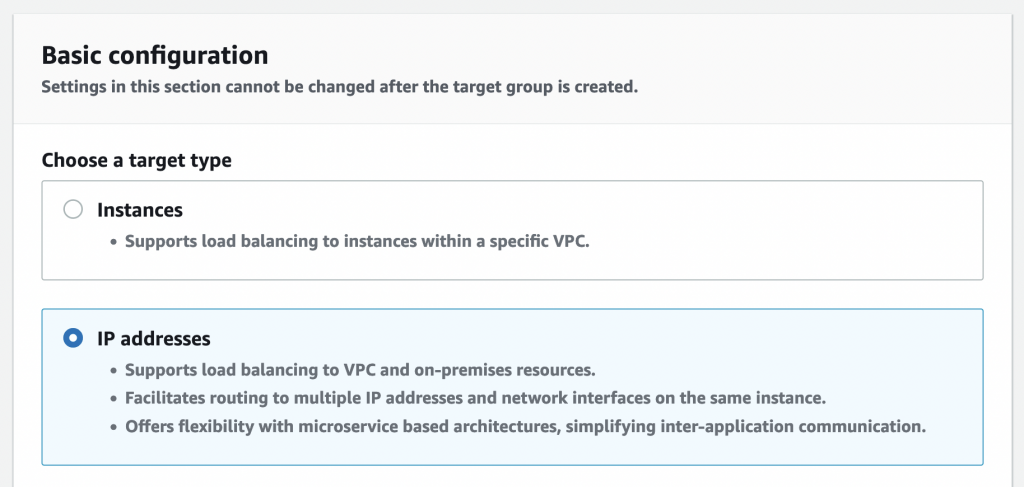
Name your target group, select TCP port 5439 & select the VPC which has your Redshift cluster:
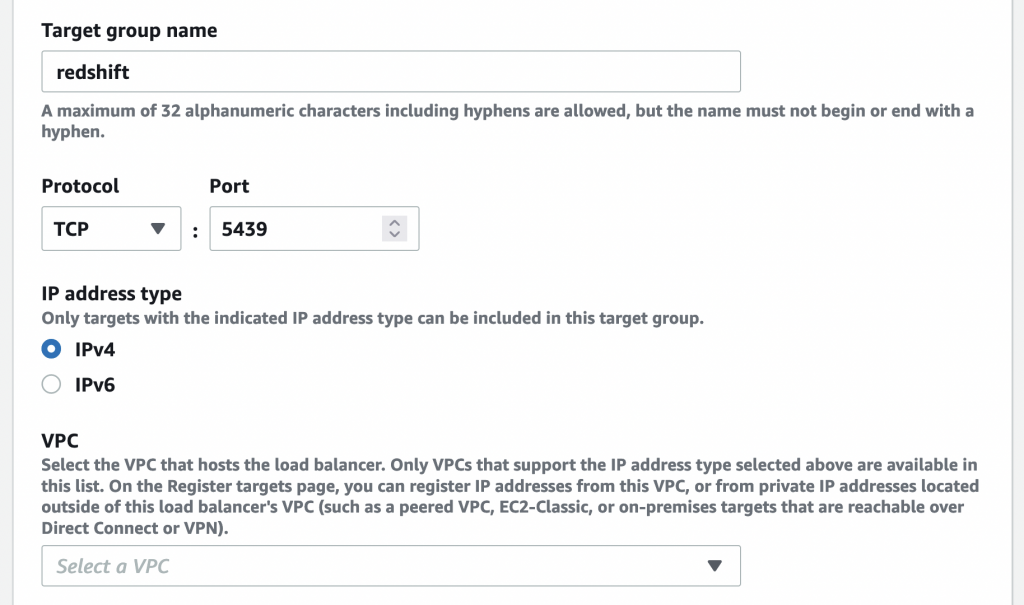
Leave the health check settings to their defaults & click Next.
In the next screen, provide the Redshift IP & click “Include as Pending Below”:
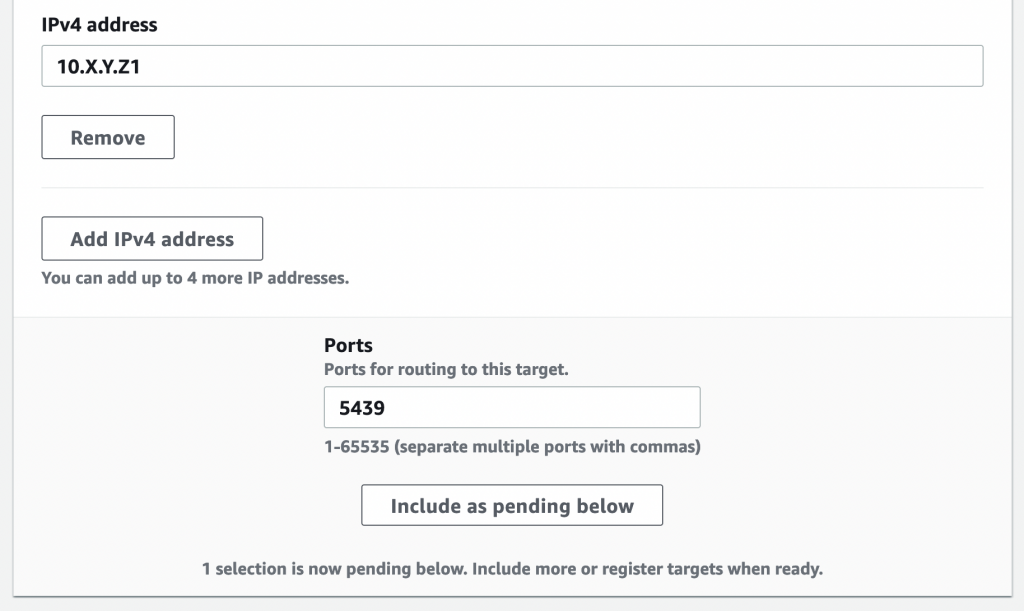
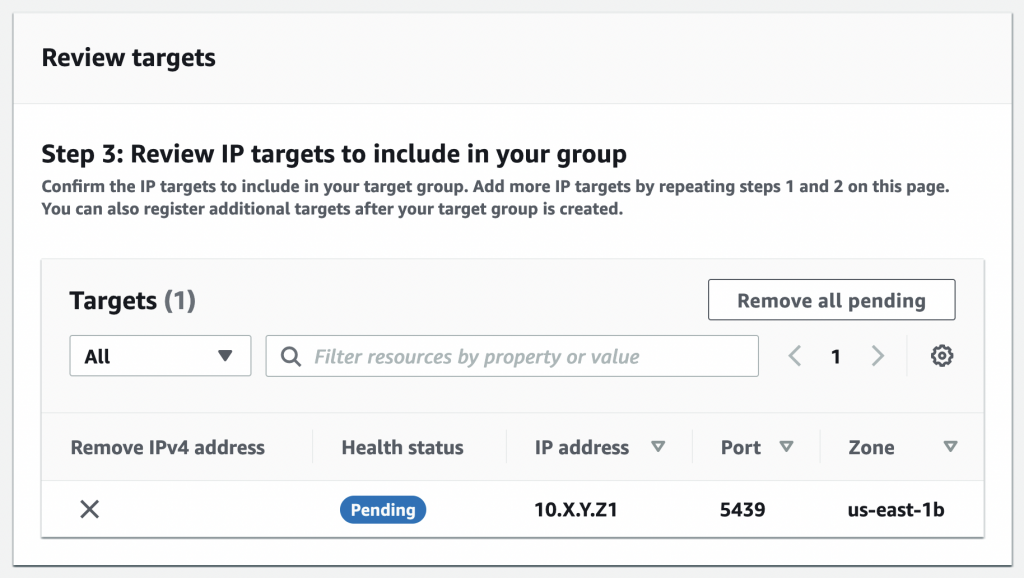
Finish creating the target group.
The Load Balancer
Next, create the network load balancer. Go to https://console.aws.amazon.com/ec2/v2/home#CreateNLBWizard:, name the load balancer, make it internet-facing, select the Redshift VPC, and provide a public subnet in each availability zone.
Create a TCP listener for Redshift’s port 5439 & forward it to the target group you created above:
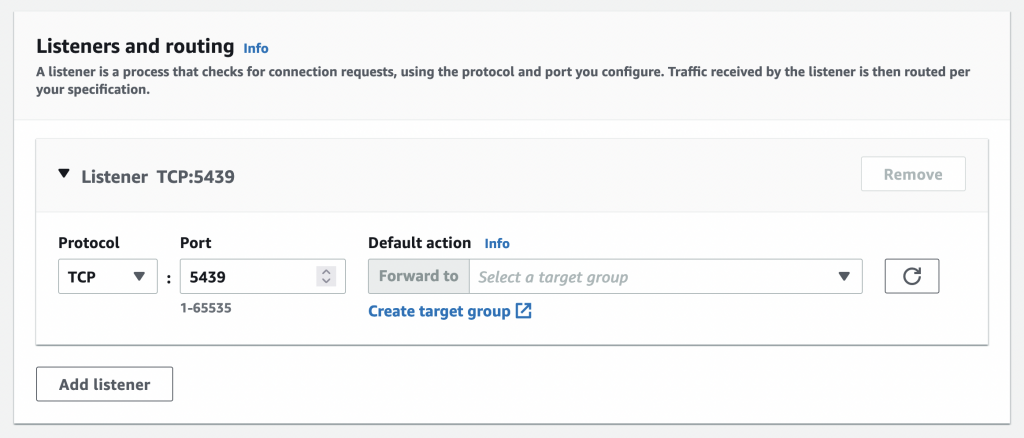
Finish creating the load balancer & wait for it to be provisioned.
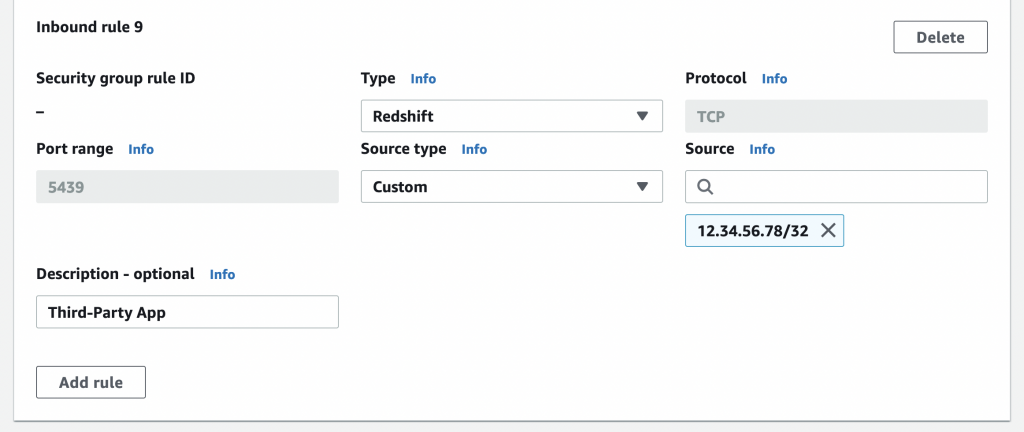
The Firewall
Network Load Balancers don’t have security groups. So you must use the target’s security group to allow/deny traffic. In our case, this means using Redshift’s security group.
Whitelist the public IPs of the third-party app in the Redshift security group:
The Connection
You can now use the NLB’s endpoint instead of Redshift’s endpoint to connect to your cluster!
About the Author ✍🏻

Harish KM is a Principal DevOps Engineer at QloudX. 👨🏻💻
With over a decade of industry experience as everything from a full-stack engineer to a cloud architect, Harish has built many world-class solutions for clients around the world! 👷🏻♂️
With over 20 certifications in cloud (AWS, Azure, GCP), containers (Kubernetes, Docker) & DevOps (Terraform, Ansible, Jenkins), Harish is an expert in a multitude of technologies. 📚
These days, his focus is on the fascinating world of DevOps & how it can transform the way we do things! 🚀






Do you know why Redshift assign a Public IP to the leader/nodes even when the cluster itself is in Private Subnet.
Here is a quote from https://docs.aws.amazon.com/redshift/latest/mgmt/managing-clusters-vpc.html#managing-clusters-in-vpc-overview
The elastic IP address is an external IP address for accessing the cluster outside of a VPC. It’s not related to the cluster node public IP addresses and private IP addresses that are displayed in the Amazon Redshift console under Connection details. The public and private cluster node IP addresses appear regardless of whether the cluster is publicly accessible or not. They are used only in certain circumstances to configure ingress rules on the remote host. These circumstances occur when you load data from an Amazon EC2 instance or other remote host using a Secure Shell (SSH) connection.