Strengthening Continuous Compliance with Security Integrations: Part 2


Table of Contents
- Introduction
- Architecture Overview
- Step-by-Step Integration and Service Roles
- Suggested Improvements (For Production Readiness)
- Conclusion
- Next Steps
- About the Author
Introduction
In Blog 1, we established a continuous compliance pipeline using AWS Config, Audit Manager, Lambda/SSM automation, and CloudWatch Dashboards. In this second part, we elevate the architecture by integrating essential AWS security services — Security Hub, GuardDuty, Amazon Macie, IAM Access Analyzer, and foundational services like CloudTrail — to provide actionable insights, threat intelligence, and compliance visibility.
This comprehensive solution is practical for small to medium workloads and includes cost estimates, detailed integration steps, and visual insights. It’s suitable for beginners and security professionals alike.
Architecture Overview
This architecture is designed to provide end-to-end compliance monitoring, security visibility, and audit readiness across your AWS environment. It combines several AWS security and management services in a coordinated flow:
- AWS Resources: Any new or existing resource (like EC2, S3, IAM roles) is continuously tracked.
- AWS Config: Acts as the foundation. It records configuration changes and evaluates them against compliance rules.
- Non-compliant resources are flagged.
- Remediation Layer (Lambda / SSM):
- Triggered by non-compliance.
- Automatically attempts to fix misconfigurations (e.g., make S3 buckets private, restrict ports on security groups).
- Security Hub:
- Ingests findings from Config, GuardDuty, Macie, IAM Analyzer.
- Provides a centralized view of security and compliance.
- Can trigger remediations via EventBridge or manual review.
- GuardDuty, Macie, IAM Access Analyzer:
- Independently scan for threats, sensitive data, and risky IAM permissions.
- Send findings into Security Hub for correlation.
- CloudTrail:
- Logs all API activity.
- Supports forensic investigations, feeds GuardDuty and Audit Manager.
- Required for visibility and evidence collection.
- Audit Manager:
- Gathers evidence from Config, CloudTrail, IAM, and Security Hub.
- Builds formal audit reports mapped to standards like CIS, PCI.
- CloudWatch Dashboards:
- Visualizes trends like compliance score, remediation status, security findings.
- Helps security and operations teams monitor posture in real time.
Please find architecture diagram as below:
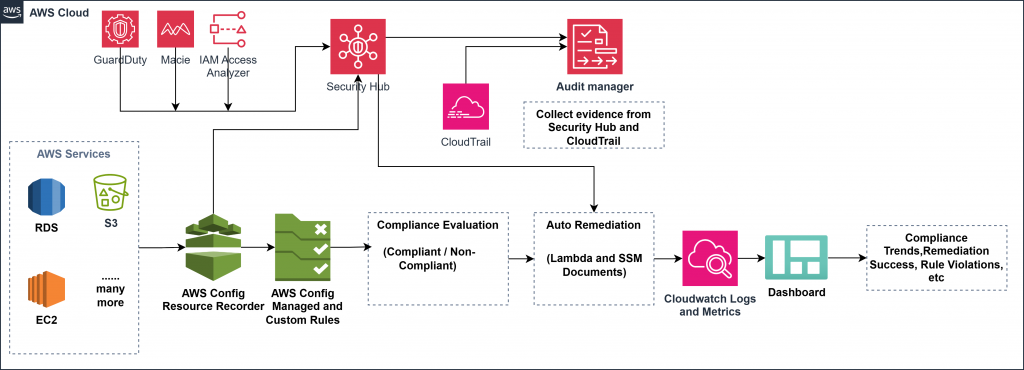
⚠️ Note: Ensure all services are enabled in the same region. While Security Hub supports multi-account and multi-region aggregation, Audit Manager and Macie must be enabled regionally.
Step-by-Step Integration and Service Roles
While the architecture flow outlines how AWS services interact, understanding the strategic role each service plays provides deeper clarity. AWS Config lays the groundwork for continuous compliance by monitoring configuration changes and evaluating them against predefined rules. These insights act as the trigger point for compliance enforcement. Security Hub steps in as the central intelligence layer, synthesizing alerts from multiple services like GuardDuty (threat detection), Macie (data sensitivity analysis), and IAM Access Analyzer (identity risk detection). The real power emerges when these findings feed into automated remediation pipelines, powered by SSM Automation and Lambda, ensuring swift, policy-driven responses. Behind the scenes, CloudTrail maintains a complete audit trail, supporting both operational transparency and forensic traceability. The final compliance lens comes from Audit Manager, which continuously gathers evidence across services to build audit-ready reports. To surface actionable insights, CloudWatch Dashboards tie everything together visually, allowing teams to monitor compliance posture, remediation trends, and security anomalies in real-time. Together, this layered approach transforms AWS into a proactive compliance ecosystem — scalable, auditable, and production-grade.
Step 1: Enable AWS Config & Define Rules
- Enable AWS Config to record resource configurations.
- Create and enable AWS Config Rules (managed or custom).
- Evaluate compliance status of supported AWS resources.
- Store snapshots and configuration history in an S3 bucket.
- This forms the foundation of the compliance and security posture.
- Make CloudTrail Role Explicit: Ensure that CloudTrail is enabled and logs API activity across the account to support Config, Audit Manager, and GuardDuty findings. CloudTrail acts as the base layer for audit trails and compliance validation.
Step 2: Automate Remediation using SSM or Lambda
- Define remediation actions using Systems Manager Automation Documents (SSM Documents) or Lambda functions.
- Link remediation to non-compliant Config Rules.
- Automate actions like removing public access, revoking excessive IAM permissions.
- Track execution status via CloudWatch.
Step 3: Enable Security Hub & Ingest Findings
- Enable Security Hub and select compliance standards.
- Integrate with:
- GuardDuty (threat detection)
- Macie (PII detection)
- IAM Analyzer (permissions analysis)
- AWS Config (compliance state)
- Bidirectional Insight Between Services: Security Hub not only ingests findings but can also influence remediation workflows via EventBridge rules. This allows a finding from IAM Analyzer to trigger automated permission revocation.
- Findings are deduplicated and scored.
- Use EventBridge to trigger notifications or remediations from critical findings.
Step 4: Enable GuardDuty, Macie & IAM Analyzer
- GuardDuty:
- Enable to monitor VPC Flow Logs, DNS queries, and CloudTrail.
- Detects anomalies like port scanning or credential exfiltration.
- Macie:
- Enable for selected S3 buckets.
- Run classification jobs to detect PII or financial data.
- IAM Access Analyzer:
- Analyze policy permissions.
- Send risky permission findings to Security Hub.
- Clarify Integration Points: Ensure CloudTrail is configured as a source for GuardDuty and Audit Manager. IAM Analyzer and Macie findings flow into Security Hub to centralize visibility and trigger alerts.
Step 5: Enable & Extend Audit Manager
Enable Audit Manager in all active regions.
- Use prebuilt frameworks like CIS or PCI, or create custom frameworks.
- Connect sources: Config, CloudTrail, IAM, and Security Hub.
- Define custom controls (e.g., Macie scans run weekly).
- Automate report generation and S3 archiving.
- CloudTrail must be enabled to collect control activity logs.
- Address Multi-Region Behavior: Ensure that CloudTrail, Security Hub, and Audit Manager are configured for region-specific or multi-region support as needed. Not all services support cross-region aggregation, so plan evidence collection accordingly.
Step 6: Visualize Everything with CloudWatch Dashboards
| Widget Title | Metric Namespace | Metric / Dimension | Purpose |
| Config Rule Compliance Trend | AWS/Config | ComplianceContributorCount (RuleName) | Track compliant vs. non-compliant resources |
| Remediation Execution Count | AWS/SSM | AutomationExecutionSuccessRate | Monitor remediation success rate |
| Audit Evidence Collected | Custom / Audit | EvidenceCount by Assessment Name | Visualize audit data collected over time |
| GuardDuty Findings Summary | AWS/GuardDuty | ThreatIntelIndicator by Severity | Show live threat alerts |
| Macie Findings Summary | AWS/Macie | SensitiveDataCount | PII and data leak alerts |
| IAM Analyzer Alerts | AWS/SecurityHub | Findings by Severity | Monitor access risks |
| Compliance by Resource Type | AWS/Config | ComplianceByResourceType | Highlight which services are non-compliant |
| Overall Compliance Gauge | AWS/Config | Aggregated NonCompliantCount | At-a-glance compliance score |
| Findings Triggered Remediation | Custom / Events | Count by Source/Severity | Validate triggered automation from Security Hub |

Service Role & Integration Table
| Service | Role | Integration | Value |
| AWS Config | Resource tracking and evaluation via rules | Lambda, SSM, Audit Manager | Core for compliance and drift detection |
| AWS Config Rules | Enforce security & governance rules | Remediation engine | Proactive misconfiguration detection |
| Lambda / SSM | Automatic remediation | Triggered via Config or Events | Reduces manual fixes |
| Audit Manager | Audit readiness and evidence gathering | Config, CloudTrail, IAM, Security Hub | Generates formal audit reports |
| Security Hub | Aggregates findings and prioritizes actions | GuardDuty, Macie, IAM Analyzer | Central view for compliance and threats |
| GuardDuty | Detects active threats | Integrated via Security Hub | Behavioral threat detection across logs |
| Macie | PII and sensitive data discovery | Findings to Security Hub | Helps achieve data privacy goals |
| IAM Access Analyzer | Reviews IAM permissions and flags risks | Integrated into Security Hub | Prevents over-privileged access |
| CloudTrail | Logs all API activity | Used by Audit Manager, GuardDuty | Base for evidence and threat detection |
| CloudWatch | Visualization and alerting platform | Custom dashboards + metrics | Central monitoring interface |
| EventBridge (Optional) | Triggers remediation or alert pipelines | Connected to Security Hub | Adds real-time response capability |
Suggested Improvements (For Production Readiness)
- Enable multi-account Security Hub aggregator for organization-wide insights.
- Use cross-region dashboards with CloudWatch Metrics Streams.
- Archive Audit Manager reports in S3 with lifecycle policies.
- Tag all compliance resources and use AWS Budgets to monitor cost.
- Enable Macie only on critical S3 buckets to optimize cost.
- Use EventBridge + Lambda to auto-remediate IAM Analyzer findings.
- Include Optional Integrations for Production:
- Integrate with AWS Organizations for centralized guardrails.
- Use AWS Security Lake for long-term event correlation.
- Connect Security Hub actions to ITSM tools like ServiceNow or Jira.
- Create a central CloudTrail for governance across accounts.
- Add monitoring for Config rule drift using Scheduled Lambda.
- Use Security Hub custom actions for integrating with ITSM tools (e.g., ServiceNow, Jira).
Cost Estimate for Continuous Compliance Solution (Monthly, Low-to-Medium Workload)
| Service | Estimated Cost (USD) | Assumptions |
|---|---|---|
| AWS Config | $6–$10 | 4 rules enabled (mix of AWS-managed and custom); ~20 resources changing daily (600 config items/month) |
| AWS Audit Manager | $30–$45 | One assessment collecting ~30,000 evidence items across services like Config, Security Hub, and CloudTrail |
| GuardDuty | $15–$30 | ~10M VPC flow logs, 100K DNS queries, and 10 GB CloudTrail logs analyzed/month |
| Macie | $50–$70 | 50 GB of sensitive data scanned across 20 S3 buckets |
| Security Hub | $5–$10 | Aggregating ~5,000 findings/month from multiple sources |
| CloudWatch | $10–$15 | 30+ custom metrics, logs ingestion (10 GB), and 3 dashboards (with retention) |
| Total Estimate | $120–$180/month | Based on AWS public pricing, no long-term discounts applied |
Conclusion
By integrating AWS Config with powerful services like Security Hub, GuardDuty, Macie, IAM Access Analyzer, CloudTrail, and Audit Manager, you lay the foundation for a production-ready, automated compliance ecosystem. This layered approach not only strengthens your organization’s security posture but also reduces manual efforts by automating threat detection, compliance evaluation, and evidence collection.
Whether you’re just starting with AWS or managing mid-sized workloads, this architecture offers immediate visibility and actionable insights, making it easier to meet audit and governance requirements. The visual dashboards and remediation-ready setup ensure that teams can respond quickly and confidently to compliance issues.
Next Steps
As you’ve now seen, integrating AWS Config with Security Hub, Audit Manager, GuardDuty, Macie, IAM Access Analyzer, and CloudWatch creates a highly observant, automated, and audit-ready security ecosystem in AWS. To take this solution further:
- Implement Remediation Pipelines
- Adopt Multi-Account/Multi-Region Strategies (Optional)
- Set Up Alerts and Notifications
- Explore Custom Audit Frameworks (Optional)
- Integrate with SIEM Tools (Optional)
- Conduct Regular Reviews and Optimization
About the Author
Deepali Sonune is a DevOps engineer with 12+ years of industry experience. She has been developing high-performance DevOps solutions with stringent security and governance requirements in AWS for 9+ years. She also works with developers and IT to oversee code releases, combining an understanding of both engineering and programming.





