Still manually suppressing security recommendations? Create Auto-suppression rules now based on your business requirements!

Managing Security Hub Noise: When and How to Use Auto-Suppression Rules Responsibly!
Table of Contents
Introduction of Security Hub
Purpose of rule creation
Prerequisite
Creation of auto suppression Rule
Cost
About the Author
Introduction of Security Hub:
AWS Security Hub provides centralized security monitoring across AWS accounts. It aggregates findings from services such as Amazon GuardDuty, Amazon Inspector, and AWS Firewall Manager, offering a unified view of your organization’s security posture.
However, as your environment grows, Security Hub can generate a significant volume of findings, ranging from critical alerts to informational notices. Managing this noise efficiently, without compromising security, becomes essential for operational effectiveness.
Purpose of rule creation:
Before diving into rule creation, it’s important to clarify: we do not recommend suppressing security recommendations indiscriminately. Every alert has a purpose, and overlooking critical findings can expose your environment to risks.
That said, there are justified scenarios where certain findings can be safely auto-suppressed, based on clearly defined business requirements and existing compensating controls. Auto-suppression in Security Hub allows you to reduce alert fatigue and focus attention on meaningful risks, while still maintaining a secure and compliant environment.
For example:
- You may receive a finding like “S3 Block Public Access setting should be enabled at the bucket-level,” but you intentionally made a bucket public for hosting static website content (such as Terms & Conditions or Policy) and that setup has already been risk-assessed and approved.
- Or consider the “Ensure Hardware MFA is enabled” recommendation. If your organization enforces Virtual MFA across all accounts through Service Control Policies (SCPs), and this has been accepted as your security baseline, suppressing this specific finding can streamline your security operations.
By implementing automated suppression rules thoughtfully, you ensure that your teams are not overwhelmed with low-risk or contextually irrelevant findings, enabling them to focus on what truly matters.
Prerequisite:
Make sure to create this Auto suppress rule to your administrator account (If you have member accounts too). Auto suppression rule can only be created, delete, edit, and view by the administrator account. A rule that an administrator creates applies to findings in the administrator account and all member accounts.
If you are not aware of the administrator account, run the following CLI command on any member account to check the administrator account.
Command: aws securityhub get-administrator-account
Creation of auto suppression rule:
- Navigate to the Security Hub service and, on the left panel, search for “Automations.”
- Give a logical name to your custom rule so it’s easy to identify, especially when you have multiple custom rules.
- Add accurate criteria based on your requirements.
Criteria:
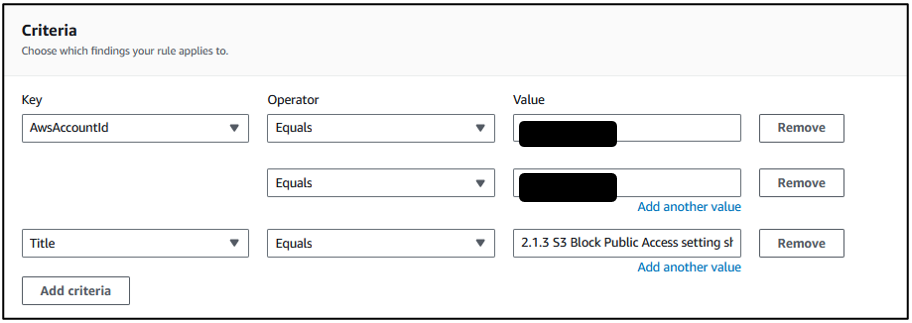
There are multiple key criteria options. Our requirement is to auto-suppress security recommendations across multiple accounts. In the Value section, you can provide the account ID(s). There is no limitation on adding Account IDs. As the Title, you can add your security recommendation. You can apply keys as per your requirements. Once you have applied keys with required data, you will see the following data.
Findings
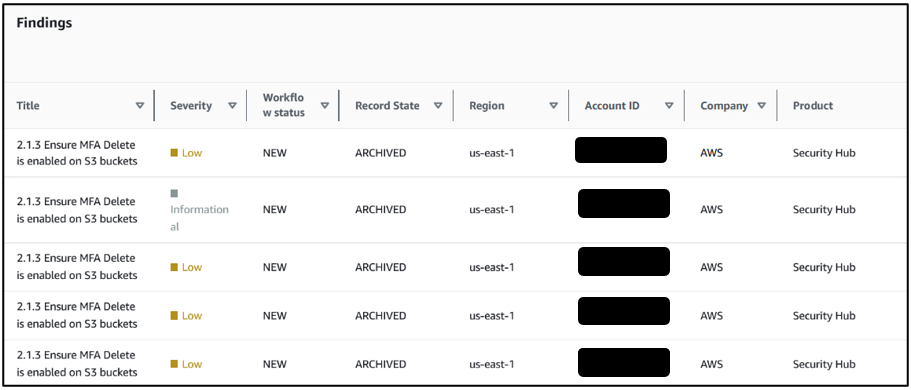
In a finding section you will see the preview of findings that match criteria. It will provide all the details related to specify recommendations.
Automated action
Next, under Automated action, specify which finding value to update automatically when findings match your criteria.
Here, we want to automatically suppress above findings. Therefore, in the automated action, we will specify “SUPPRESSED.”
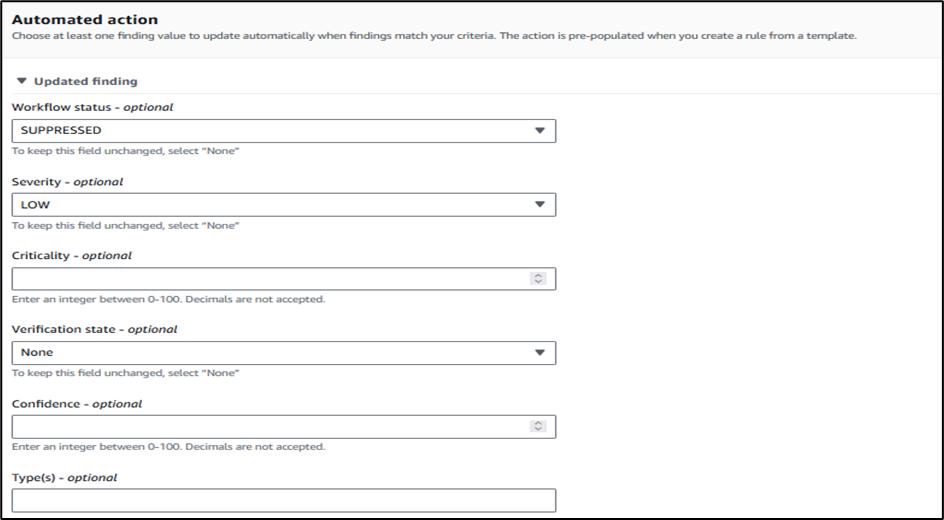
Rule Status:
For rule status, choose Enabled, and then choose Create rule.

Before hitting to create rule option make sure to review all the configuration. Once a rule is created and enabled, it will start executing based on the conditions specified.
Cost:
The cost depends on the number of criteria you select for your rule. Several factors affect the pricing for an auto-suppression rule:
Below are the factors on these pricing will work for Auto suppression Rule.
- Number of accounts
- Number of Security Checks per Account
- Number of Finding Ingested per Account
- Number of Automation Rules
- Number of criteria in each automation rule
Let’s consider a scenario with 4 accounts, 25,000 security checks, 1,000 findings ingested per account, 1 automation rule, and 2 criteria. In this case, the monthly cost is estimated to be between $100 to $150.
To determine the precise cost for your rule, use the AWS Pricing Calculator to calculate the pricing for your automated rule based on your specific requirements.
About the Author:

Madhavi Khadye is a Cloud Engineer at QloudX with 2.7 years of hands-on experience in AWS. She holds both the AWS Certified Solutions Architect – Associate and AWS Certified Security – Specialty certifications.
Madhavi specializes in Cloud Security and Cost Optimization, bringing expertise in conducting over 10 AWS Well-Architected Reviews (WARs) and successfully remediating High-Risk Issues (HRIs) for all of them. Her proactive approach to security and operational excellence makes her an integral part of the QloudX team, ensuring robust, secure, and cost-effective AWS solutions for clients.
In tag: AWS, Automation, AWS Security Hub, AWS Security Recommendations and Flow, Cost monitoring and analysis.





